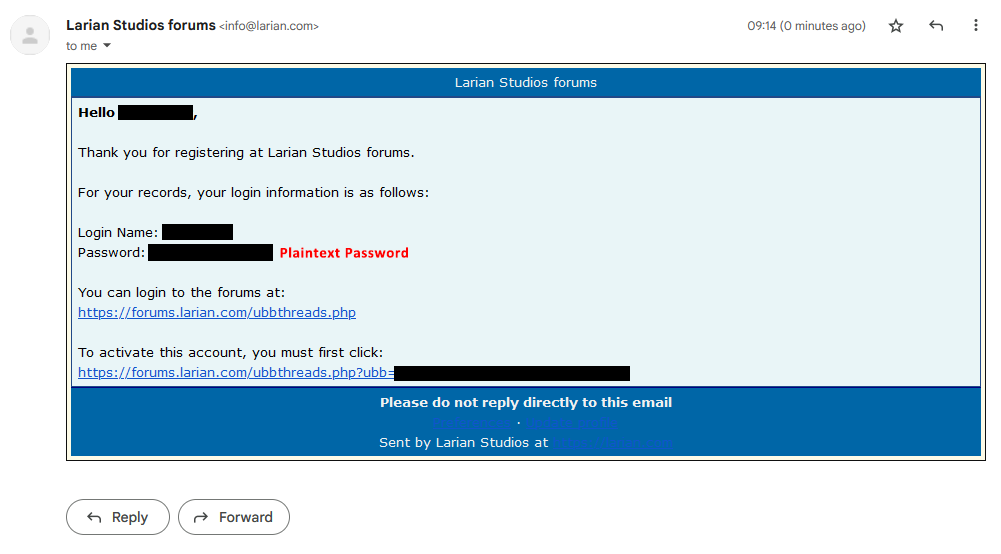
Hello, c/Games mod here.
This post has been reviewed as valid by the mod team
For everyone infosec culture, hashing and salting password consist in using one-way mathematical functions to encrypt passwords. It is a very commonly used security practice to make it more difficult for an attacker that was able to steal a database to obtain the password. As the website is unable to decrypt said password (thank to the one way mathematical function), the only way to send you back your password in this manner is to have it unhashed and unsalted in his database.
But
In the current case, this is a registration email, which may have been sent before the initial hashing and salting. In this case we cannot say for sure if Larion Studios indeed have unhashed and unsalted password in his database.