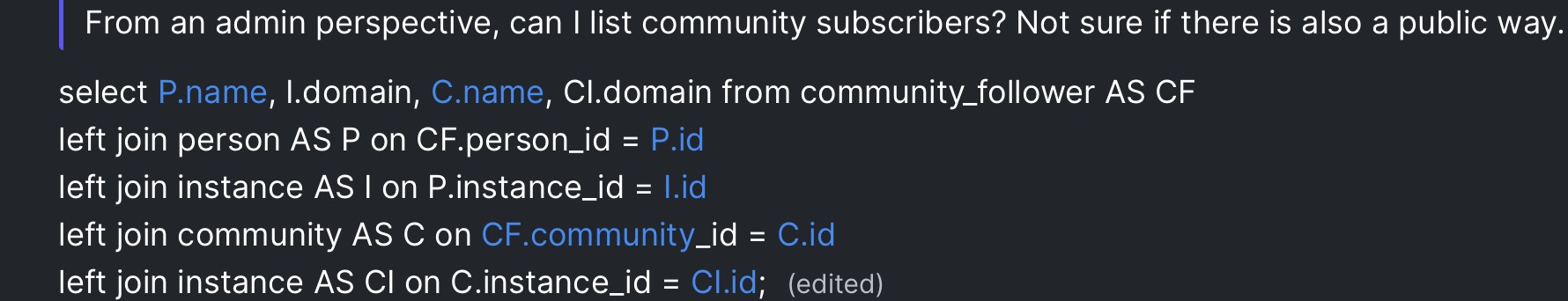
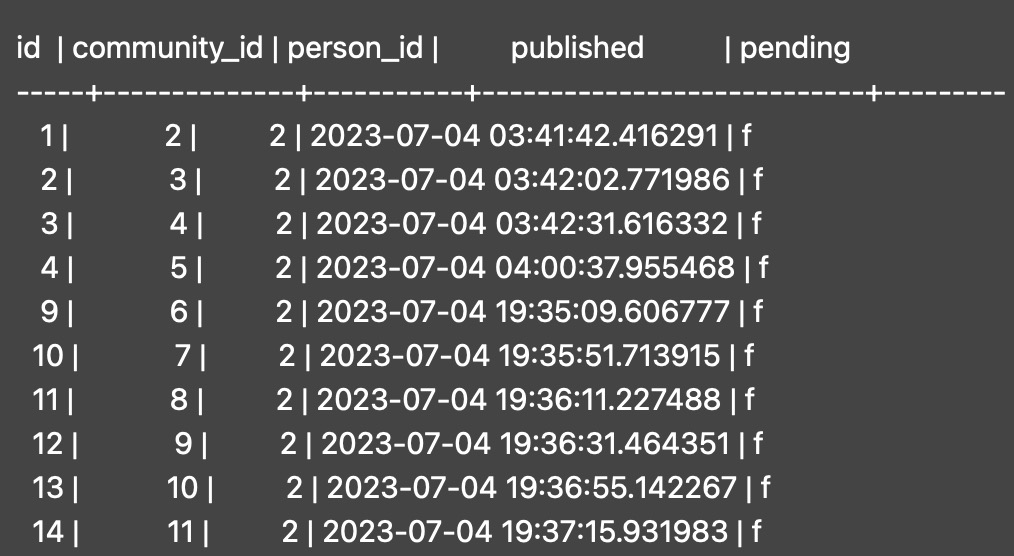
There's no reasonable way around it. The best that can be done would to anonymize the votes but then there's nothing preventing a rogue instance from reporting "yup, 500 users have upvoted this".
Tying the votes to an account can be helpful mitigating spam. Bots can analyze your patterns and based on your account age, comment history and what not, establish whether you're a legit user. If everything is anonymous, there's nothing that can be done.
ActivityPub was just not designed with privacy in mind. There's debates as to whether Lemmy can possibly be GDPR compliant at all.
Keys would not help at all here, you just switch it from a user ID to a public key.
Either we have trusted mega instances, or we have complete transparency.